This is part nine of a multi-part series reviewing Canada’s Anti-Spam Legislation in practice since its introduction in 2014 and the beginnings of enforcement in 2015. Crosslinks will be added as new parts go up.
Part 1: Terminology
Part 4: Case File – Compu-Finder
Part 5: Case File Anthology, 2015-2016
Part 6: Case File – Blackstone Education
Part 7: Case File Anthology, 2017-2018
Part 8: Case File – Brian Conley/nCrowd
Part 9: Case File Anthology, 2019-2022
Core resources:
Enforcement Actions Table (CASL selected)
December 12, 2019
A $115,000 AMP issued for violations of s9 of CASL against John Paul Revesz and Vincent Leo Griebel, partners, Orcus Technologies.
This is one of the rarer cases of malware under CASL; in this case the Orcus Remote Administration Tool (RAT) found by the CRTC’s Chief Compliance and Enforcement Officer to be a remote access trojan, a type of malware, confusingly also with the acronym RAT.1I don’t know if Orcus was being cute with the name, or this is just a coincidence.
This, in combination with the sale of a DDNS (dynamic domain name server) service to hackers to allow them to communicate with RAT-infected computers, resulted in two NOVs for Revesz and Griebel2Nerd note: if you’re going to be a villain, take a hard look at your last name, put the word “Darth” in front of it, and see how it sounds. If it’s credibly somebody who would wear all black and whack at people with a lightsaber, reconsider your whole deal. resulting in $115,000 in penalties — $100,000 for developing, selling and promoting malware, and an additional $15,000 for the DDNS service.
A news story on this, from Krebs on Security, a security consultant’s site.
It’s pretty open and shut: clear evidence of what the RAT did, clear evidence of both Revesz and Griebel bragging on hacking forums about its ability to steal information and passwords.
Note that at the time this AMP was issued, it was for section 9 of CASL:
It is prohibited to aid, induce, procure or cause to be procured the doing of any act contrary to any of sections 6 to 8.
Canada’s Anti-Spam Legislation, s9
Per the NOV, an investigation was still underway to determine if the RAT actually been installed without consent on systems, which would be a violation of section 8:
8 (1) A person must not, in the course of a commercial activity, install or cause to be installed a computer program on any other person’s computer system or, having so installed or caused to be installed a computer program, cause an electronic message to be sent from that computer system, unless
(a) the person has obtained the express consent of the owner or an authorized user of the computer system and complies with subsection 11(5); or
(b) the person is acting in accordance with a court order.
Canada’s Anti-Spam Legislation, s8
…and unlock penalties up to $1,000,000.
The Orcus RAT seems to be alive and well as an open-source piece of software for jerks to try to use.
Some mysteries here:
The NOV has a February 2020 update that states that the time for response expired, so the issued AMP becomes enforceable:
Update 17 February 2020: Pursuant to section 24(1) of CASL, the deadline to make representations with respect to either the amount of the penalty or the acts or omissions constituting the alleged violations was February 3, 2020. Given that no representations were made, pursuant to section 24(2) of CASL, John Paul Revesz is deemed to have committed the violations and must pay the administrative monetary penalty as set out in the notice.
Where’s Griebel? Per this news story, he’s German, so that might be why he was dropped.
Stranger still: where’s the criminal charge?
$115,000 in penalties should be the least of Revesz and Griebel’s worries (if Griebel is still in play). Cybercrime is a thing, and the abovementioned news stories mention criminal charges filed by the RCMP. But the links in the stories to the 2019 RCMP press release go to a 404 page. It’s not a broken link; searching their news, there’s nothing for Revesz, Griebel or Orcus.3Testing the search function, by comparison, there’s 4,385 results for “Grand Falls,” which I used as a test because it was mentioned in the top story – now I’m deeply worried about what in God’s name is going on in Grand Falls.
There’s nothing in CanLII showing any court action: nothing relevant for the search terms Revesz, Griebel, or Orcus. Similarly nothing in WestLaw or Lexis.
When I hit the Wayback Machine, I can find an archive of the news release.
UPDATE: thanks to the incredible assistance and sleuthing of the Queen’s Law Library team, I have been pointed to upcoming court dates for a John Revesz. Whether or not these are related (or even the same John Revesz; no middle name here) isn’t confirmed.
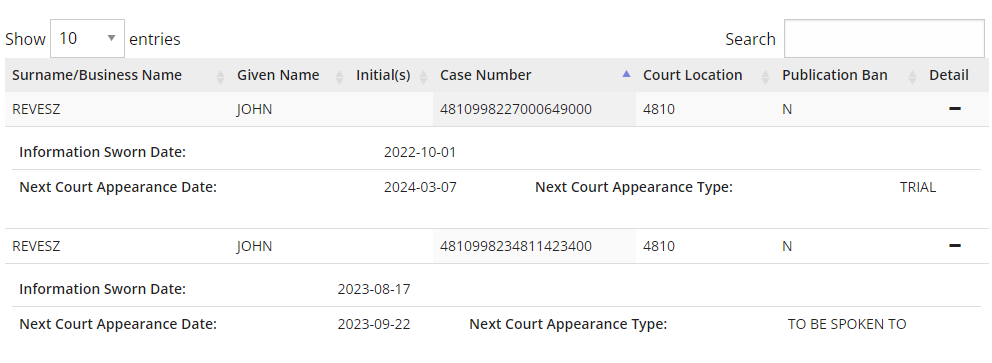
The Orcus RAT was first outed as malware in July of 2016, with Revesz and Griebel posting openly about its utility to hackers. It even looks like Krebs did the heavy investigative lifting for the government.
A 30-month delay between this becoming public knowledge and action being taken to stop it by Canadian authorities – and then, seemingly only $115,000 in penalties – is worrisome. The lack of any charges – or delay in bringing charges – is worrisome.
If CASL is the only mechanism taken against a Canadian promulgating hacking tools, that’s troubling. The scope of these is CASL, and I don’t want to go too far down a rabbit hole about how cybercrime is prosecuted, but a scheme designed at its heart to deal with spam shouldn’t be our first and last line of defense against malware created and propagated here in Canada.
And – finally – the fact that this is only $15,000 more than Conley and nCrowd is an eyebrow-raiser as well. In the latter case, a very scammy cluster of shady companies sent out a lot of spam emails to try to get people to buy deal coupons of very limited utility. In this case, malware was unleashed on the Canadian public and promoted to hackers globally. The consequences of buying a bad coupon from a deals site versus giving hackers total access to your computer, which could easily extend to identity theft and all your banking information, is a huge gulf.
This doesn’t feel like a $15,000 swing to me, but that might be attributable to the fact that this is only a s9 violation and an investigation is still, per the NOV from almost four years ago, underway to see if Revesz also violated s8.
If nothing else, this has convinced me to keep my antivirus and malware checkers up to date.
Issued penalty: $115,000
Final penalty: $115,000
Total issued AMPs: $2,782,000
Total imposed AMPs/monetary penalties: $1,068,250
Differential: $ 1,713,750
September 21, 2020
What is it with not-quite-education companies in this space? Compu-Finder, Blackstone, and now a $100,000 penalty levied against OneClass, a service that connects students with user-generated study guides, lecture notes and video tutorials. Decision here, plus a press release.
This seems open and shut: OneClass sent CEMs without recipient consent, and (allegedly) installed a Chrome extension that harvested personal information including usernames and passwords on students’ computers. U of T still has a news piece up instructing students of the phishing email: in essence, it looks like it would access the user’s Blackboard class lists to send emails to all classmates inviting them to join OneClass. The U of T item also has instructions on how to remove it. As phishing goes, this is on the spammy but not super harmful end of things.
Issued penalty: $100,000
Final penalty: $100,000
Total issued AMPs: $2,882,000
Total imposed AMPs/monetary penalties: $1,168,250
Differential: $ 1,713,750
March 29, 2021 / January 4, 2022
A 2021 notice of violation and $75,000 AMP for Scott William Brewer, later reduced to $7,500 in payment in 2022.
Brewer committed violations in two categories – affiliate marketing, earning a commission from CEMs sent without consent to recruit people to an online gambling site, casinoonlinesoftware.com, and direct web marketing for his own online marketing and web business.
The CRTC apparently only investigated three of Brewer’s campaigns, topping 600K emails, despite
Corroborating information reviewed during the investigation indicated that Brewer may have been responsible for sending, causing or permitting to be sent, several million non-compliant CEMs. During a sample period in the investigation, approximately 11 million emails were sent from Brewer’s IP address over a 24 day period.
This, called a “hailstorm campaign,” prompted a press release from the CRTC claiming this as the “largest ever penalty to an individual for sending messages without consent”. Which seems odd, as Brian Conley was subject to $100,000 under vicarious liability for similar violations two years before. Key quote from the Chief Compliance and Enforcement Officer from that release:
“Spam campaigns, such as those carried out by Mr. Brewer, are disruptive to Canadians and undermine their confidence in electronic commerce. Obtaining consent is a fundamental principle of Canada’s anti-spam legislation. The penalty issued today demonstrates that individuals are just as accountable as businesses and must respect this principle.”
And then, 10 months later, it’s no longer a $75,000 penalty, but one for 10% of that amount. The final undertaking says:
Brewer cooperated with the CCEO, provided new information not previously available to the designated person, and has voluntarily agreed to resolve the CCEO’s outstanding concerns regarding compliance with the Act and the Regulations (CRTC).
And later, that the $7,500 penalty
…fully and completely resolves all outstanding issues between the Commission and Scott William Brewer with respect to his compliance with the Act and the Regulations (CRTC) in relation to the CCEO’s investigation into the sending of CEMs during the period of 1 December 2015 to 23 May 2018 and up to the effective date of this undertaking.
Scott seems to be doing fine, with a business pivot to site-building for SEO and sales conversions, per his LinkedIn profile.
Issued penalty: $75,000
Final penalty: $7,500
Total issued AMPs: $2,957,000
Total imposed AMPs/monetary penalties: $1,175,750
Differential: $ 1,781,250
December 6, 2021
A $200,000 imposed AMP to the Gap, for a marketing campaign including its subsidiaries Banana Republic and Old Navy – CEMs without consent and without an unsubscribe mechanism.
Gap seems to have agreed with the CCEO, agreed to pay, and implement a compliance program.
No specifics in the NOV, unlike previous decisions that articulated a number of campaigns or messages; here’s the decision in full:
Undertaking: Gap Inc., File No.: 9110-2021-00605
Undertaking: Gap Inc.
File No.: 9110-2021-00605
Effective date of undertaking: 6 December 2021
Monetary payment amount: $200,000
Under section 21 of An Act to promote the efficiency and adaptability of the Canadian economy by regulating certain activities that discourage reliance on electronic means of carrying out commercial activities, and to amend the Canadian Radio-television and Telecommunications Commission Act, the Competition Act, the Personal Information Protection and Electronic Documents Act and the Telecommunications Act, S.C. 2010, C. 23 (CASL, or the Act)
Person entering into an undertaking
Gap Inc.
Acts and omissions covered by the undertaking and provisions at issue
Gap Inc. has voluntarily entered into an undertaking with the Chief Compliance and Enforcement Officer (CCEO) concerning alleged violations of paragraphs 6(1)(a) and 6(2)(c) and subsections 11(1) and 11(3) of the Act.
Following an investigation, the CCEO alleged that commercial electronic messages (CEMs) were sent or caused to be sent by Gap Inc., between 7 January 2018 and 11 August 2021 to promote sales for Gap Inc. as well as for subsidiaries Banana Republic and Old Navy, without consent from recipients and/or not including an unsubscribe mechanism which could readily be performed,.
Amount owing and summary of other conditions
During the course of the investigation, Gap Inc. has cooperated with the CCEO. Gap Inc. has voluntarily undertaken, pursuant to section 21 of the Act, to resolve the CCEO’s outstanding concerns regarding Gap Inc.’s compliance with the Act and the Electronic Commerce Protection Regulations (CRTC), SOR/2012-36 (the Regulations (CRTC)), including undertaking to comply with, and ensuring that any third party authorized to send a CEM complies with the Act and Regulations (CRTC).
As part of this undertaking, Gap Inc. agreed to make a monetary payment of $200,000 to the Receiver General for Canada in accordance with subsection 28(3) of the Act.
In addition to the monetary payment, and in order to promote compliance with the Act and the Regulations (CRTC), Gap Inc. undertakes to update its compliance program addressing the sending of CEMs. This compliance program has included or will include:
corporate compliance policies and procedures;
training and education for employees of Gap Inc.; and,
monitoring, auditing and reporting mechanisms.
In addition, Gap Inc. will monitor and review its policies and procedures to determine whether any have the effect of providing incentives for employees to violate the Act and the Regulations (CRTC) and, if so, Gap Inc. undertakes to eliminate such incentives.
Gap Inc. will also develop and provide periodic training programs, which include compliance procedures and processes to comply with Act, for employees involved with commercial electronic messages and related compliance.
Finally, Gap Inc. will register and track CEM complaints and the subsequent resolution of those complaints. Gap Inc. will also implement effective corrective measures for compliance failures and within six months of the effective date of the undertaking will supplement the information it has already provided to the CCEO of the corrective measures already implemented to date, as well as information supporting any updates to its Compliance Program.
This undertaking fully and completely resolves all outstanding issues between the Commission and Gap Inc. with respect to Gap Inc.’s compliance with the Act and the Regulations (CRTC) in relation to the CCEO’s investigation into the sending of CEMs for the period up to and including the effective date of this undertaking.
Straightforward.
And here, for the last time (as of August 2023, with the Brewer decision in 2022 being the final one reported4UPDATE: This is no longer true; there is a July 2023 AMP, reported in late October 2023: 18 months since the last reported CASL enforcement decision, which is the longest gap in its history.), is the tally:
Issued penalty: $200,000
Final penalty: $200,000
Total issued AMPs: $3,157,000
Total imposed AMPs/monetary penalties: $1,375,750
Differential: $ 1,781,250
The difference between the imposed and issued penalties is greater than the penalties imposed, which is interesting.
A quick stop off with a relatively recent NOV, and then we’ll sum all this up.
- 1I don’t know if Orcus was being cute with the name, or this is just a coincidence.
- 2Nerd note: if you’re going to be a villain, take a hard look at your last name, put the word “Darth” in front of it, and see how it sounds. If it’s credibly somebody who would wear all black and whack at people with a lightsaber, reconsider your whole deal.
- 3Testing the search function, by comparison, there’s 4,385 results for “Grand Falls,” which I used as a test because it was mentioned in the top story – now I’m deeply worried about what in God’s name is going on in Grand Falls.
- 4UPDATE: This is no longer true; there is a July 2023 AMP, reported in late October 2023: 18 months since the last reported CASL enforcement decision, which is the longest gap in its history.